Comprehensive USB control that’s easy to manage
Immediate USB device visibility, granular control, and protection at your fingertips.Immediate USB device visibility, granular control, and protection at your fingertips.
Mitigate malware risk
‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾
Gain the granular control needed to enable safe USB device use and prevent the spread of malware.
Track every move
‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾
Easily monitor and track approved USB device use with visibility into USB data and file activity.
Streamline policy management
‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾
Easily manage policies through intuitive dashboards. No extra agents, software, or hardware required.
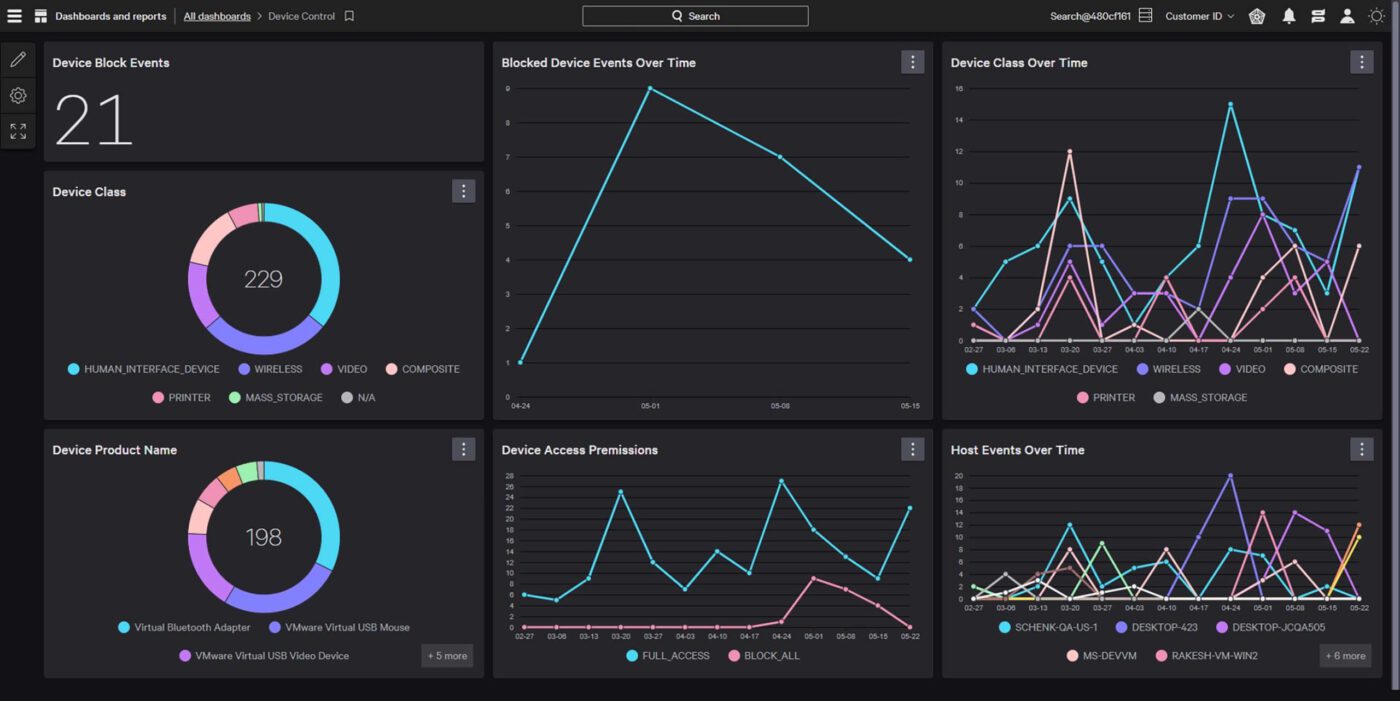
See all USB activity
View comprehensive file metadata and USB activity context to easily detect and investigate data loss and exfiltration. With detailed user and device information, ZIP archive introspection, and Microsoft sensitivity labels, you gain the visibility you need for a proactive defense.
Identify and safeguard source code
Detect source code movement with precision. Advanced machine learning watches over 40 source code languages, catching any sign of exfiltration. Simple, effective, and relentless — your intellectual property is safeguarded against threats.
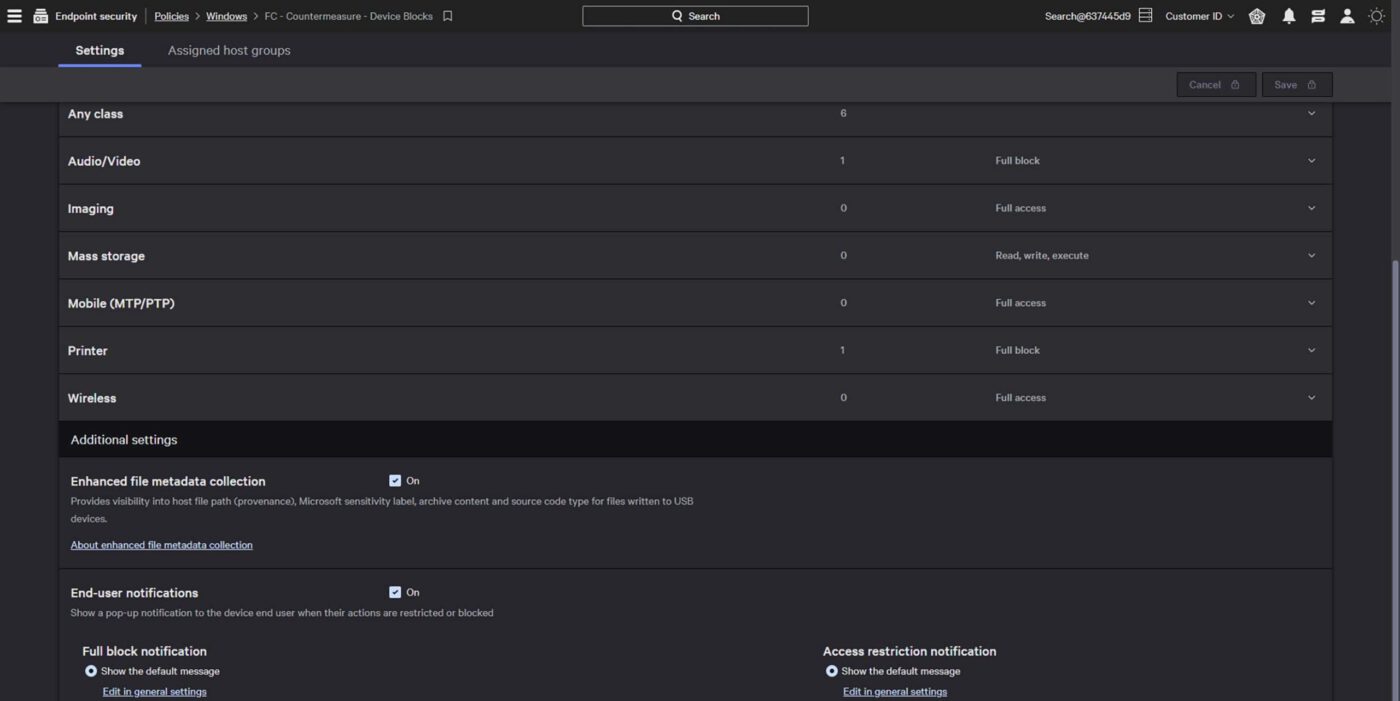
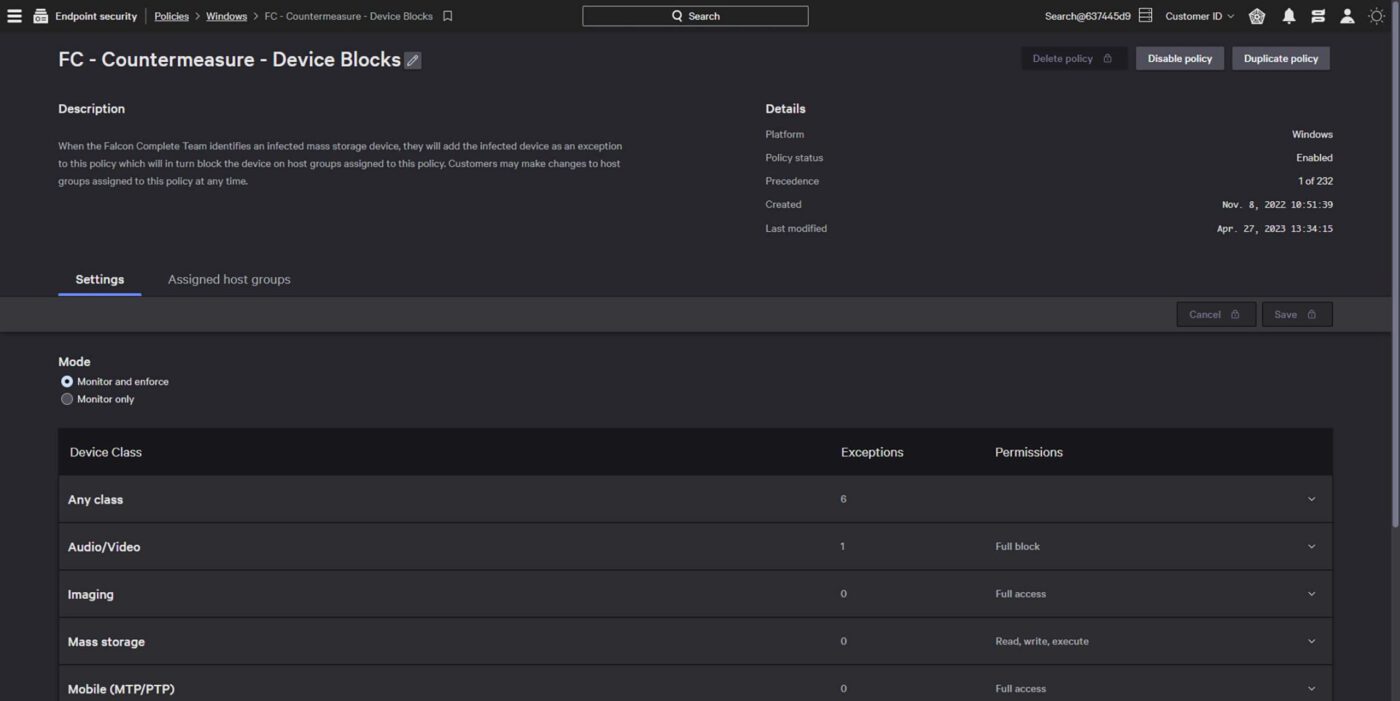
Precise and granular control
Implement granular access rights to ensure only approved external USB devices are used. Simple workflows accelerate policy creation and allow analysts to test policy impacts prior to enforcement, eliminating potential disruption.
Featured resources